PCI Proxy
A PCI Proxy is a service that allows companies to handle payment card data securely, complying with the Payment Card Industry Data Security Standard (PCI DSS). The primary goal of a PCI Proxy is to protect sensitive payment card data (such as credit and debit card numbers) by ensuring that businesses do not store or process this data directly, thereby reducing their scope of PCI DSS compliance.
The PCI DSS is a set of security standards designed to protect cardholder information and prevent fraud, data breaches, or unauthorized access.
What Does a PCI Proxy Do?
A PCI Proxy acts as an intermediary between the business and sensitive payment data (e.g., credit card numbers, CVV codes). Instead of the company storing or processing this information directly, the proxy:
- Tokenizes Sensitive Data: It transforms sensitive data (like card numbers) into a token, which is an identifier that has no value if intercepted.
- Routes Information: It sends data to secure processing systems, such as payment providers, without the sensitive data passing through the company's servers.
- Ensures PCI DSS Compliance: By eliminating the need for businesses to handle sensitive data directly, it facilitates compliance with the stringent PCI DSS security standards.
The proxy serves as an additional layer of security to protect payment data.
Benefits
- PCI Compliance: By not storing or processing sensitive data, businesses reduce the number of requirements they need to meet for PCI DSS compliance. This simplifies the audit and regulatory processes.
- Reduced Risk: The proxy ensures that sensitive data never touches the merchant's servers, minimizing the risk of data compromise. This is crucial for protecting against data theft and cyberattacks.
- Simplified Integration: By using a PCI Proxy, companies can integrate more quickly with payment platforms without dealing with the complexity of PCI DSS compliance certifications.
How Does It Work?
- Tokenization: Card data is sent to the PCI Proxy which returns a token instead of actual card details.
- Token Usage: The token can be used securely in future transactions.
- Secure Processing: The token is forwarded to payment processors, keeping your infrastructure free from sensitive data exposure.
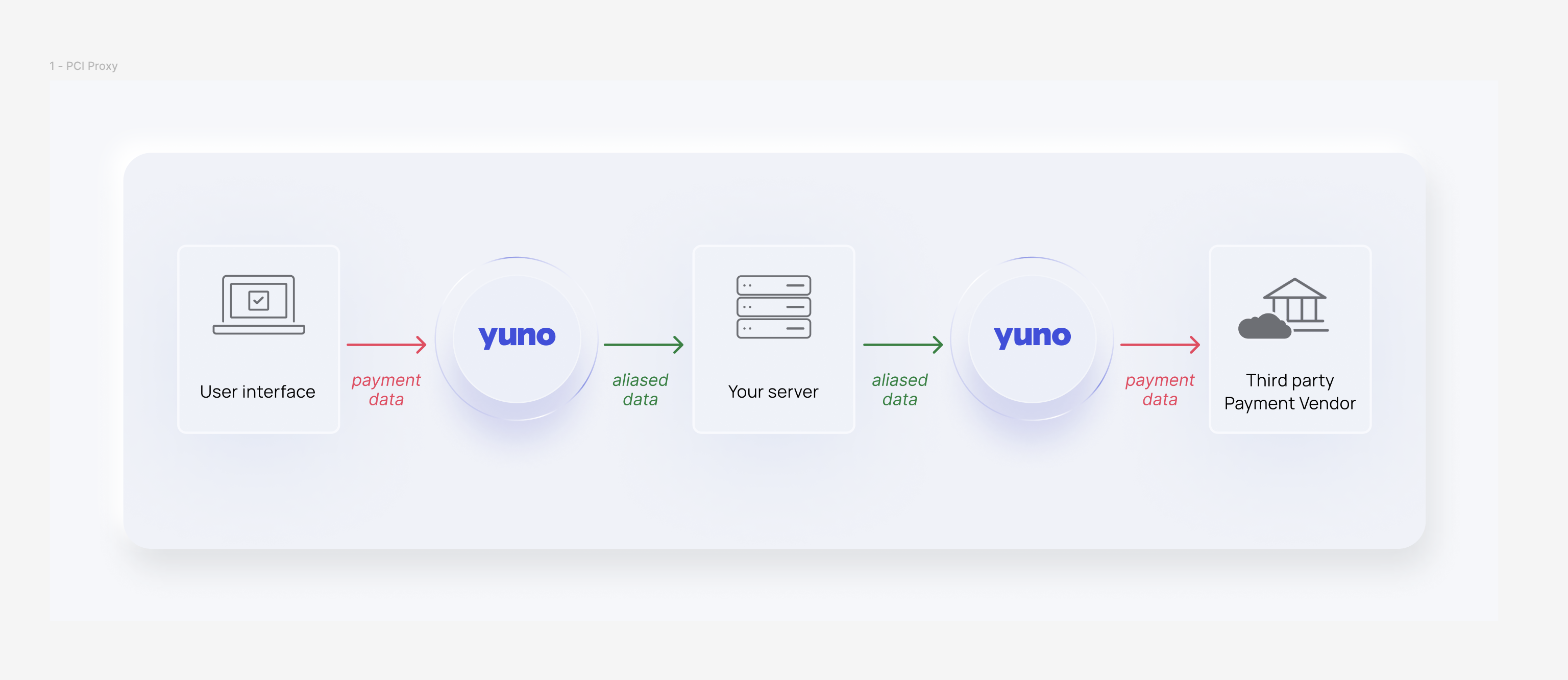
Integration with Yuno
However each service at Yuno can be utilized independently to meet our merchants' needs, this guide outlines how to use the instruments and tokens stored in our Vault with your own payment service, ensuring that your infrastructure remains protected from sensitive data.
Step 1: Tokenize information
In Yuno you have multiple ways of tokenizing/enrolling credit card information depending on your requirements.
- Enroll credit cards with our PCI Compliant SDKs
- Enroll credit cards directly to our payment methods API.
Once you have done the enrollment for each case, you will receive a vaulted_token that represents the card information in our vault will be necessary for the payment creation.
Step 2: Create Payments
Once you have your vaulted_token you can create payments directly to our pci-proxy API specifying the provider you want to process with.
Before using the /pci-proxy endpoint, you must inform Yuno about the provider you wish to exchange information with.
First, we need to verify their PCI certification to ensure the secure handling of full PANs. Yuno will conduct specific checks on the provider before transmitting card data to maintain security and compliance for everyone involved. Once these security checks are completed, we can proceed to set up the provider in our system. For instance, we need to know the endpoint on the provider's side that we should call on your behalf (providerUrl) and the credentials required for authentication (providerConfig).
After Yuno has confirmed their compliance, we will assign you a provider Id to identify the provider within our system, as well as a providerConfigId that contains your unique credentials for making calls. Both of these identifiers will be necessary to carry out proxy requests.
- Endpoint:
api.y.uno/pci-proxy/[provider_id] - Request body: The same as you would send directly to the provider but with certain keys to replace the card information expected.
- Card number: [[vaulted_token.card_number]]
- Cardholder Name: [[vaulted_token.cardholder_name]]
- Expiration Month: [[vaulted_token.expiration_month]]
- Expiration Year: [[vaulted_token.expiration_year]]
- Response: The same as you would receive from the provider.
This process ensures data never reaches your infrastructure without passing through tokenization, thus maintaining the highest security standards in payment processing.
Updated 6 months ago