Okta SSO Guide
This guide explains how to connect Yuno to Okta using SAML 2.0.
Prerequisites
- An Okta account
- An application for use with Yuno
- Admin privileges in Okta to manage SSO settings
- Access to the Yuno dashboard
Step 1: Create a SAML application in Okta
In Okta, go to:
Applications → Create App Integration → SAML 2.0 → Next
Select a name for your application and, optionally, upload a logo. You will then see the SAML configuration form.
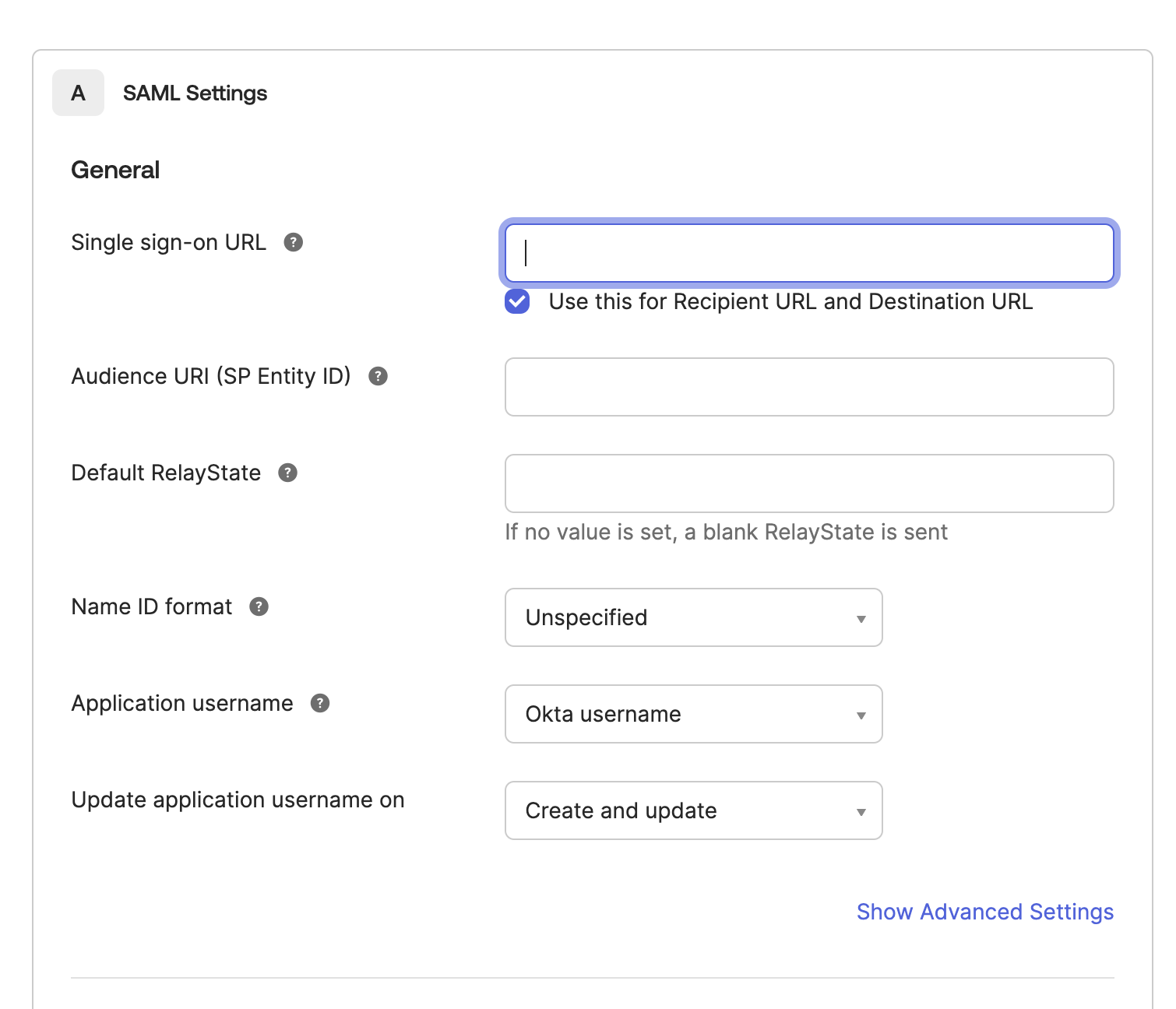
Step 2: Configure SAML settings using Yuno values
Open the Yuno dashboard, click your profile image, then open Security. Navigate to the Single Sign-On (SSO) tab, click Set up, and gather this info:
- Identifier (Entity ID)
- Assertion Consumer Service URL
Copy these values into the Okta SAML form:
- Audience URI (SP Entity ID) → Identifier (Entity ID)
- Single sign-on URL → Assertion Consumer Service URL
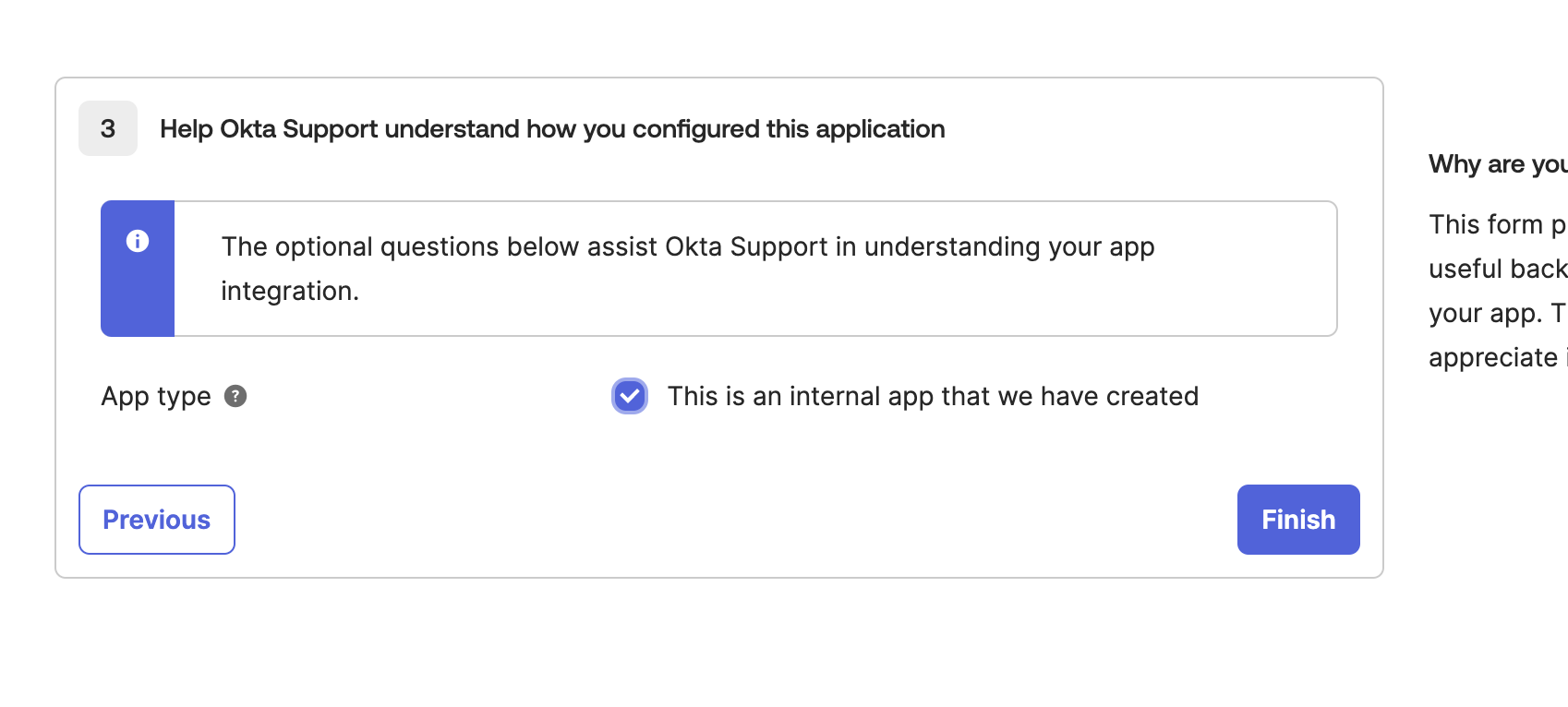
Click Next, then check the option This is an internal app…, and finish the setup.
Step 3: Export and upload the metadata XML
In Okta, locate the Metadata URL under the application’s settings and open it. Save the file as metadata.xml.
Then, in the Yuno dashboard:
- Upload the
metadata.xmlfile under Yuno configuration → Option A: Upload metadata XML - Wait for the Upload completed confirmation
- Click Save
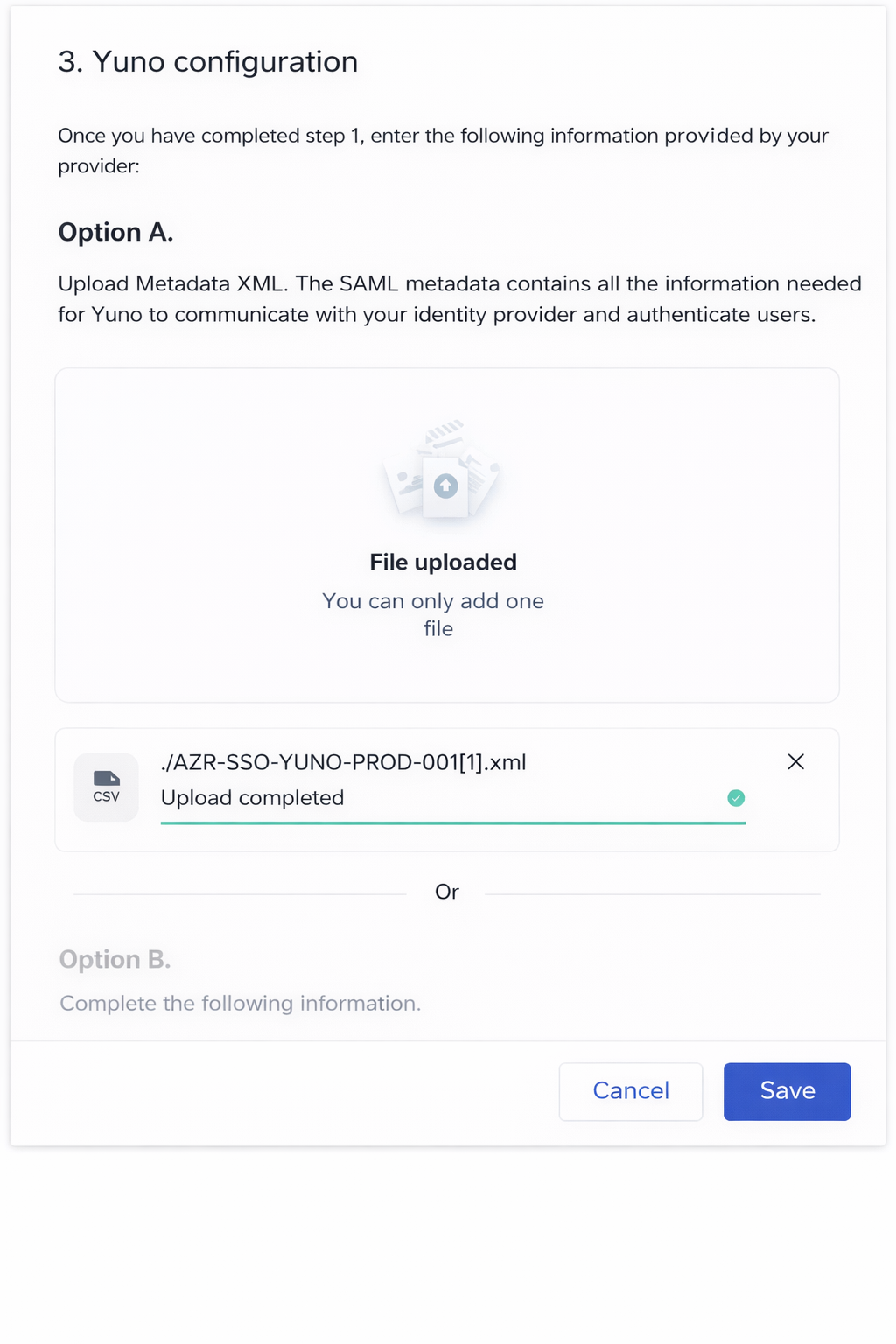
Alternatively, you can take the information listed in Option B and enter it manually.
Step 4: Assign users in Okta (optional)
Once configuration is complete, you can assign Okta users or groups to the application so they can log in using SSO.
Troubleshooting
If you cannot set up the SSO connection or run into issues after initial configuration:
- Yuno requires signed SAML responses, check:
- Both the SAML response and the assertion are signed
- The signing algorithm configured in Okta is SHA-256
- The certificate used for signing matches the one included in the metadata
- Review SSO logs in the Yuno dashboard under Security → Single sign-on (SSO)
Updated 2 months ago